Silent Ransom Group targeting law firms, the FBI warns
Security Affairs
MAY 24, 2025
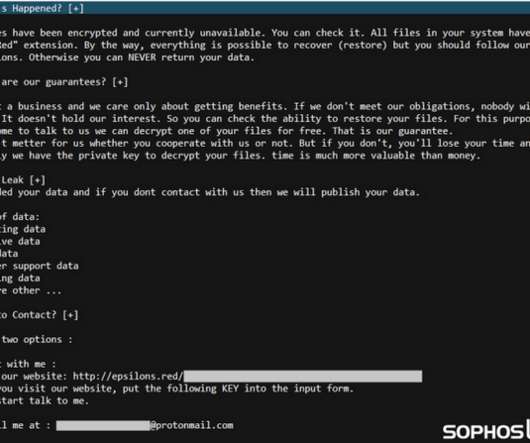
“The cyber threat actor Silent Ransom Group (SRG), also known as Luna Moth, Chatty Spider, and UNC3753, is targeting law firms using information technology (IT) themed social engineering calls, and callback phishing emails, to gain remote access to systems or devices and steal sensitive data to extort the victims.”












































Let's personalize your content