What do Cyber Threat Actors do with your information?
Zigrin Security
OCTOBER 11, 2023
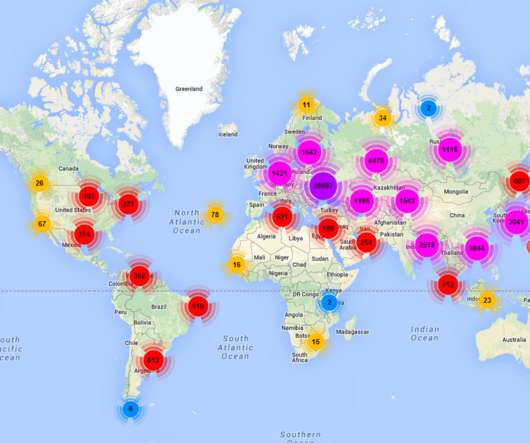
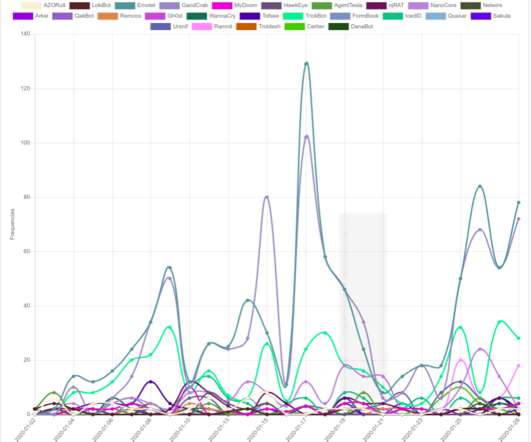
State-sponsored hacking is a growing concern, with governments using cyberattacks to gather intelligence, disrupt infrastructure, or compromise national security. Hacktivism and Ideological Motives Hacktivism refers to hacking activities undertaken for ideological or political reasons. The first one is selling it on the dark web.












































Let's personalize your content