Nation-State Attacker of Telecommunications Networks
Schneier on Security
OCTOBER 22, 2021
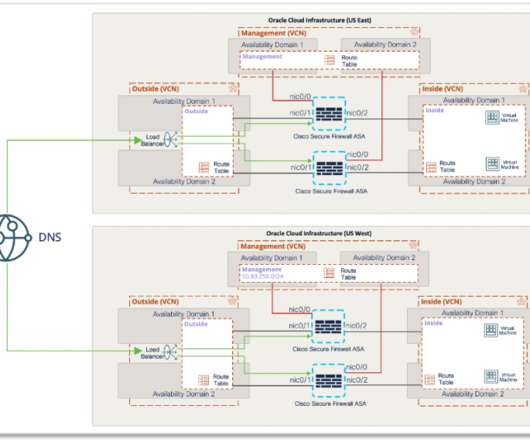
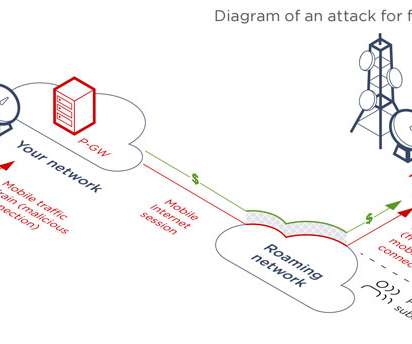
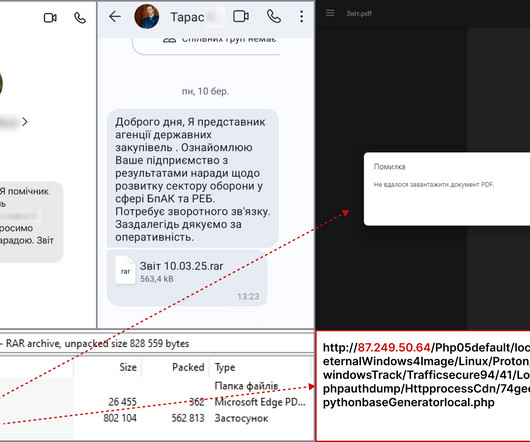
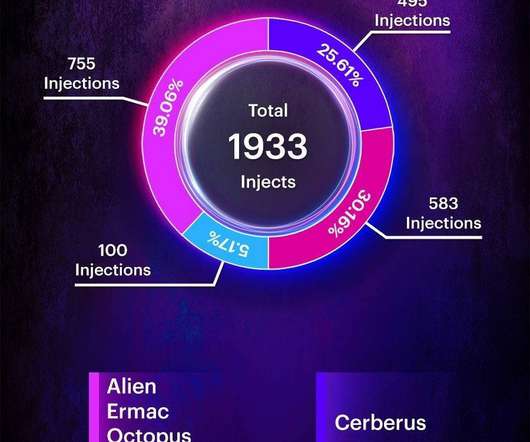
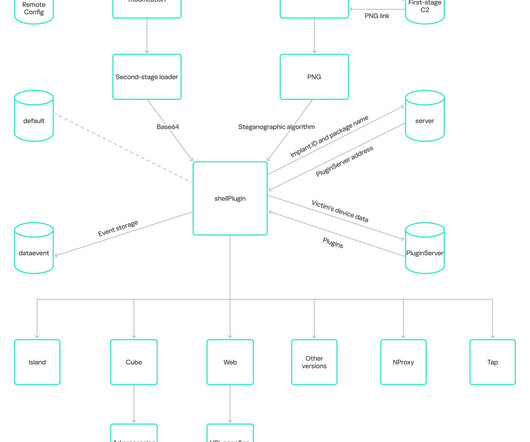
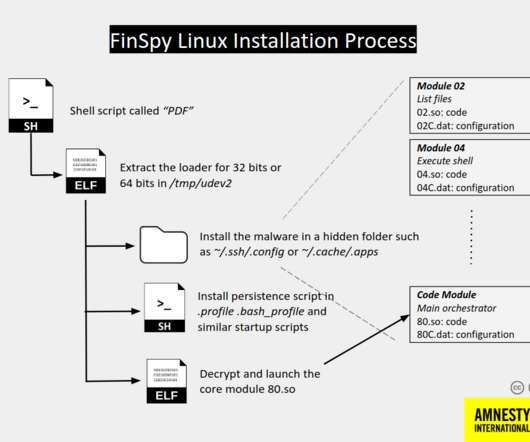
Someone has been hacking telecommunications networks around the world: LightBasin (aka UNC1945) is an activity cluster that has been consistently targeting the telecommunications sector at a global scale since at least 2016, leveraging custom tools and an in-depth knowledge of telecommunications network architectures.









































Let's personalize your content