Email Security Guide: Protecting Your Organization from Cyber Threats
CyberSecurity Insiders
APRIL 16, 2023
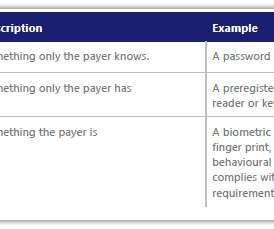
Ransomware attacks via email: Ransomware is a type of malware that encrypts an organization’s data, holding it hostage until a ransom is paid. Multi-factor authentication (MFA): MFA is a security measure that requires users to provide multiple forms of identification to access email accounts and other sensitive systems.


















































Let's personalize your content