Cisco Confirms Data Breach, Hacked Files Leaked
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.

IT Security Guru
OCTOBER 26, 2023
Enter Two-Factor Authentication, or 2FA for short. Here’s a shocking stat: according to the Verizon Data Breach Investigations Report , 81% of hacking-related breaches leverage either stolen or weak passwords. Always use VPN for your safety to protect your data from prying eyes. What Exactly is 2FA?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
APRIL 28, 2024
From March 18, 2024, to April 16, 2024, Duo Security and Cisco Talos observed large-scale brute-force attacks against a variety of targets, including VPN services, web application authentication interfaces and SSH services.

Security Affairs
FEBRUARY 16, 2024
The threat actor compromised network administrator credentials through the account of a former employee that was used to successfully authenticate to an internal virtual private network (VPN) access point. The threat actor likely obtained the employee’s account credentials from a third-party data breach.

Security Affairs
JANUARY 13, 2024
NAS (Network-Attached Storage) servers that are often used for backups on the network have been hacked and wiped, as have automatic tape backup devices, and in almost every case we know of, all backups have been lost. Cisco investigated the hacking campaign with the help of Rapid7. concludes the alert.

Security Affairs
JANUARY 13, 2024
Akira ransomware targets Finnish organizations GitLab fixed a critical zero-click account hijacking flaw Juniper Networks fixed a critical RCE bug in its firewalls and switches Vast Voter Data Leaks Cast Shadow Over Indonesia ’s 2024 Presidential Election Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467 Team Liquid’s wiki leak exposes (..)

Security Affairs
OCTOBER 21, 2023
Okta says that threat actors broke into its support case management system and stole authentication data, including cookies and session tokens, that can be abused in future attacks to impersonate valide users. HAR files can also contain sensitive data, including authentication information. ” concludes the advisory.

Security Affairs
JANUARY 13, 2024
NAS (Network-Attached Storage) servers that are often used for backups on the network have been hacked and wiped, as have automatic tape backup devices, and in almost every case we know of, all backups have been lost. Cisco investigated the hacking campaign with the help of Rapid7. concludes the alert.

The Last Watchdog
MARCH 6, 2021
Related: Poll confirms rise of Covid 19-related hacks. Set-up 2-factor authentication. If somehow passwords are leaked, a hacker can cause a data breach. Two-factor authentication or two-step verification involves adding a step to add an extra layer of protection to accounts. Use antivirus software.

Security Affairs
JULY 27, 2023
This would make it extremely complicated for the company to inform its clients about a data breach or to warn them of malware attacks,” researchers said. What DepositFiles data was exposed? The exposed file had credentials for the Redis database, allowing anyone to read, edit, or delete data stored there.

Security Affairs
JUNE 23, 2020
CLOP ransomware operators have allegedly hacked IndiaBulls Group , an Indian conglomerate headquartered in Gurgaon, India. CLOP ransomware operators have allegedly hacked the Indian conglomerate IndiaBulls Group , its primary businesses are housing finance, consumer finance, and wealth management. . Pierluigi Paganini.

Krebs on Security
MAY 19, 2020
In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” For more on this dynamic, please see The Value of a Hacked Email Account.

Security Affairs
SEPTEMBER 12, 2022
Upon achieving an MFA push acceptance, the attacker had access to the VPN in the context of the targeted user. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user. . SecurityAffairs – hacking, Cisco). Pierluigi Paganini.

Security Affairs
MAY 9, 2021
Experts found critical authentication bypass flaw in HPE Edgeline Infrastructure Manager UNC2529, a new sophisticated cybercrime gang that targets U.S. Experts found critical authentication bypass flaw in HPE Edgeline Infrastructure Manager UNC2529, a new sophisticated cybercrime gang that targets U.S. Pierluigi Paganini.

Security Affairs
AUGUST 7, 2022
of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4 of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4 SecurityAffairs – hacking, newsletter). Pierluigi Paganini.

Security Affairs
NOVEMBER 29, 2020
SecurityAffairs – hacking, newsletter). Pierluigi Paganini. The post Security Affairs newsletter Round 291 appeared first on Security Affairs.

IT Security Guru
MARCH 28, 2023
Having a cybersecurity plan ensures that you remain protected against data breaches, phishing scams , and other cybercrimes. On top of that, turn on two factor authentication. Use a VPN Using a VPN is essential when working with sensitive data or files.
Security Affairs
MAY 11, 2023
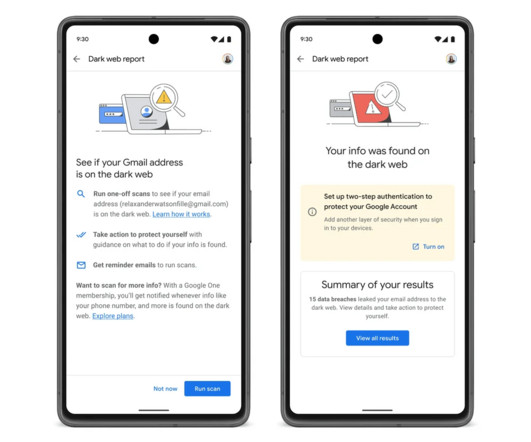
Once an email address is discovered on the dark web, Google will urge users to enable two-step authentication (2FA) to protect their Google accounts. Google also announced the availability of VPN access for all Google One plans. The upcoming feature will be also extended to users from select international markets. We are in the final!

CyberSecurity Insiders
DECEMBER 6, 2022
When employees aren’t in the office, they’re liable to engage in risky behaviors such as using unsecured WiFi without a VPN, leaving work devices unlocked in public places, and clicking on malicious emails. Companies should also provide clear channels for reporting suspicious incidents.

Krebs on Security
JULY 10, 2022
Twice in the past month KrebsOnSecurity has heard from readers who’ve had their accounts at big-three credit bureau Experian hacked and updated with a new email address that wasn’t theirs. “I was able to answer the credit report questions successfully, which authenticated me to their system,” Turner said.

CyberSecurity Insiders
DECEMBER 18, 2021
Use Strong Passwords & Two-Factor Authentication. If your password is exposed in a data breach, you must change it immediately. Websites might inform you via e-mail when such breaches occur, but with a considerable delay. Avoid reusing them across other websites, no matter how unimportant.

Webroot
FEBRUARY 15, 2024
If you’ve been compromised in a data breach, hackers can use your stolen email and password to try and enter thousands of other sites—and if you keep using the same credentials, they’ll be successful. Use two-factor authentication Two-factor authentication adds an extra layer of security to your online accounts.
Security Affairs
APRIL 23, 2022
The VPN credentials for initial access are said to have been obtained from illicit websites like Russian Market with the goal of gaining control of T-Mobile employee accounts, ultimately allowing the threat actor to carry out SIM swapping attacks at will. SecurityAffairs – hacking, T-Mobile). ” wrote Krebs. Pierluigi Paganini.
Security Affairs
SEPTEMBER 10, 2020
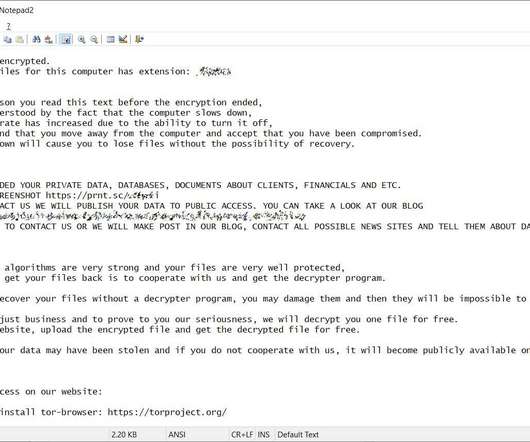
. “LOOK AT THIS SCREENSHOT [link] IF YOU NOT CONTACT US WE WILL PUBLISH YOUR DATA TO PUBLIC ACCESS. “The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation.” Consider installing and using a VPN.

Security Affairs
APRIL 3, 2022
Sophos Firewall affected by a critical authentication bypass flaw Mar 20- Mar 26 Ukraine – Russia the silent cyber conflict Security Affairs newsletter Round 358 by Pierluigi Paganini Western Digital addressed a critical bug in My Cloud OS 5 CISA adds 66 new flaws to the Known Exploited Vulnerabilities Catalog. Pierluigi Paganini.

CyberSecurity Insiders
SEPTEMBER 14, 2021
This does not bode well for their longevity, as other industry data shows that 60% of small businesses that suffer a data breach will be out of business within six months. Use of a VPN – virtual private networks (VPN) create a secure connection to other networks over the internet.

Duo's Security Blog
APRIL 20, 2023
Australia is no stranger to this rising concern, with recent reports indicating a rise in the number and severity of breaches. One such report: The latest Office of the Australian Information Commissioner (OAIC) Notifiable data breaches report for July through December of last year.

CyberSecurity Insiders
OCTOBER 29, 2021
A few simple changes to your devices and accounts can help discourage cyber criminals from trying to access your data. Prevent Data Breaches. Giants like Facebook and Target have suffered breaches and password leaks, so it’s safe to say data from at least one of your online accounts could have been leaked.

CyberSecurity Insiders
JULY 21, 2021
According to Verizon’s 2021 Data Breach Investigations Report , credentials are the type of data cybercriminals most want to steal in a breach. For example, as many companies continue to allow employees to work remotely, VPNs are becoming more and more crucial. Let’s take a closer look at a few of those habits.

Security Affairs
MAY 7, 2021
In fact, attackers often don’t even need to hack them to steal all that precious data: one of the most common causes of a breach are databases that have been simply left unsecured, allowing anyone to access the data without providing a username or password. Can’t come up with a strong password?

Security Affairs
DECEMBER 8, 2019
Data of 21 million Mixcloud users available for sale on the dark web. Twitter account of Huawei Mobile Brazil hacked. A flaw in Microsoft OAuth authentication could lead Azure account takeover. CVE-2019-14899 flaw allows hijacking VPN connections on Linux, Unix systems. The best news of the week with Security Affairs.

Hot for Security
JUNE 14, 2021
In many cases, no malware is needed to compromise this data. iPhones are not immune to hacks. It can intercept messages, perform keylogging activities, steal Google Authentication codes, and it even enables its authors to take full remote control of a user’s phone.

Hacker Combat
JULY 31, 2020
Sure, this might sound like something that doesn’t need to be said, but a surprising number of data breaches occur because people neglect to treat security as a priority. Employ Multi Factor Authentication (MFA). Compromised, reused and weak passwords are responsible for 81 percent of hacking related breaches.

IT Security Guru
APRIL 20, 2023
A security-aware one may have thought, what’s the chance of someone hacking my email vs. me finishing this work by Monday? Pretty unlikely I’ll get hacked, so I choose work. When you’re managing an environment where the average cost of a data breach is $4.18 What if someone copies sensitive data into another file?

Adam Levin
NOVEMBER 17, 2020
Mobile payment platforms, like Apple Pay and Google Pay, use advanced technology, like fingerprint authentication and tokenization (in which credit card account numbers are replaced by randomly generated numbers) to provide brick-and-mortar shoppers with an added layer of security. Enable two-factor authentication.

Security Affairs
JULY 29, 2022
Therefore, strong authentication methods are needed. Therefore, strong authentication methods are needed to improve security without hindering user convenience. What is Strong Authentication? The IAM Security Boundary Strong authentication is a critical component of modern-day identity and access management.

SC Magazine
MAY 12, 2021
One catalyst pre-dates the pandemic and was more of a slow burn: a gradual understanding that mainframes are no longer “special” or “unique” when it comes to hacking and data breaches. The world has changed. To the bad folks, it’s just another computer. And we do so securely.

Security Affairs
MARCH 15, 2023
The leak also included the JWT secret key, another type of token, which is usually used for authentication. Additionally, the company should consider whether the platform needs to be accessible through the internet or only through a VPN, which would provide an additional layer of security.
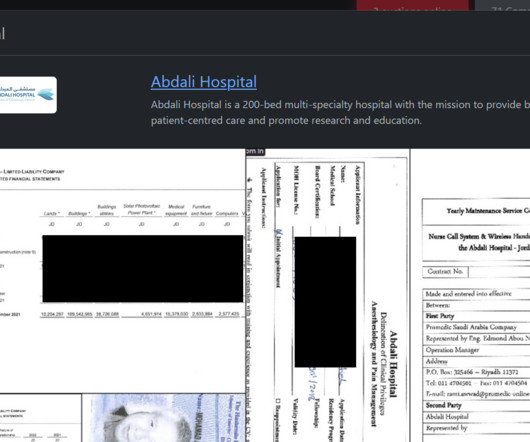
Security Affairs
DECEMBER 26, 2023
The Rhysida ransomware group claimed to have hacked Abdali Hospital, a multi-specialty hospital located in Jordan. pic.twitter.com/6uHMDcNhTC — Dominic Alvieri (@AlvieriD) December 26, 2023 The group published images of stolen documents as proof of the hack. Open your wallets and be ready to buy exclusive data.

Security Boulevard
MAY 12, 2022
Insurance carriers will offer a variety of different policies and coverage, including: Costs associated with an actual data breach, including letters to all affected victims. Critical — Multi-factor Authentication (enabled) — Least Privileged (Predictive). Critical — Secure EDP/VPN access- (Predictive).
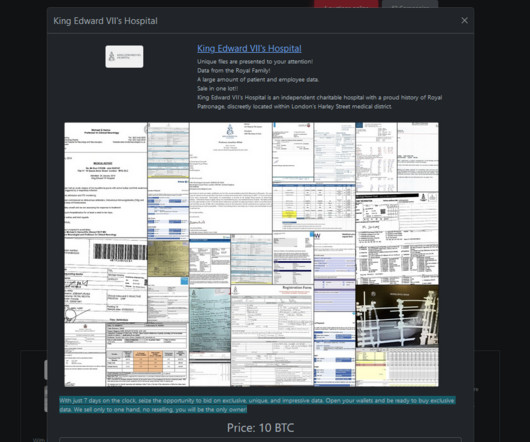
Security Affairs
NOVEMBER 29, 2023
The Rhysida ransomware group claimed to have hacked King Edward VII’s Hospital in London. The Rhysida ransomware group claimed to have hacked King Edward VII’s Hospital in London and added it to the list of victims on its Tor leak site. King Edward VII’s Hospital in London has been breached by Rhysida Ransomware.

Krebs on Security
APRIL 6, 2022
Many organizations are already struggling to combat cybersecurity threats from ransomware purveyors and state-sponsored hacking groups, both of which tend to take days or weeks to pivot from an opportunistic malware infection to a full blown data breach. In fact, the group often announces its hacks on social media.

SiteLock
AUGUST 27, 2021
Cybercriminals know this, which is why phishing attacks account for more than 80% of reported security incidents and why 54% of companies say their data breaches were caused by “negligent employees. ”. Default passwords are usually available online and hackers can search remotely for vulnerable equipment to hack.

Security Affairs
FEBRUARY 4, 2024
Clorox estimates the costs of the August cyberattack will exceed $49 Million Mastodon fixed a flaw that can allow the takeover of any account Iranian hackers breached Albania’s Institute of Statistics (INSTAT) Operation Synergia led to the arrest of 31 individuals Ex CIA employee Joshua Adam Schulte sentenced to 40 years in prison Cloudflare breached (..)
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content