Securing the IoT at Scale: How PKI Can Help
Security Boulevard
MAY 27, 2022
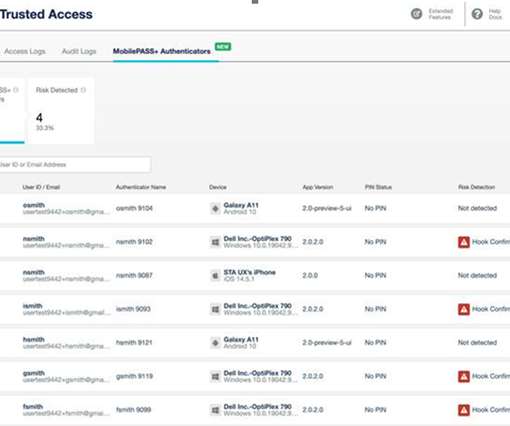
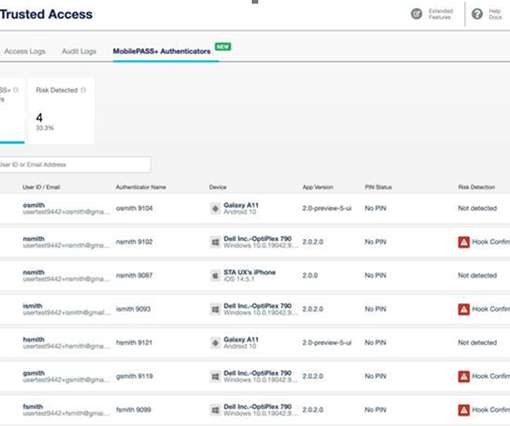
Manufacturers need a scalable solution to address concerns like authentication, data encryption, and the integrity of firmware on connected devices. Security in IoT devices has lagged behind their production. The post Securing the IoT at Scale: How PKI Can Help appeared first on Keyfactor.














































Let's personalize your content