Gmail client-side encryption: A deep dive
Google Security
JUNE 29, 2023
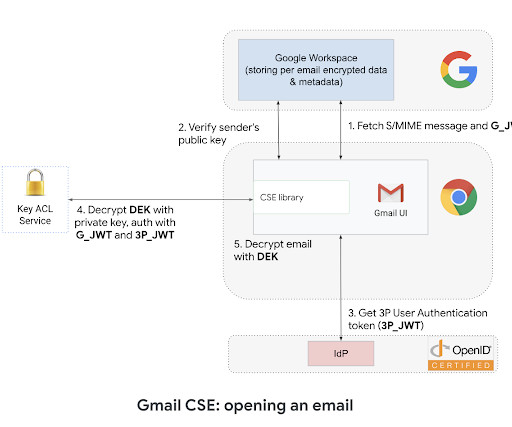
Director of Engineering, Google Workspace In February, we expanded Google Workspace client-side encryption (CSE) capabilities to include Gmail and Calendar in addition to Drive, Docs, Slides, Sheets , and Meet. When CSE is enabled, email messages are protected using encryption keys that are fully under the customer’s control.













































Let's personalize your content