RAID Technology and the importance of disk encryption in data security
Pen Test Partners
JANUARY 3, 2024
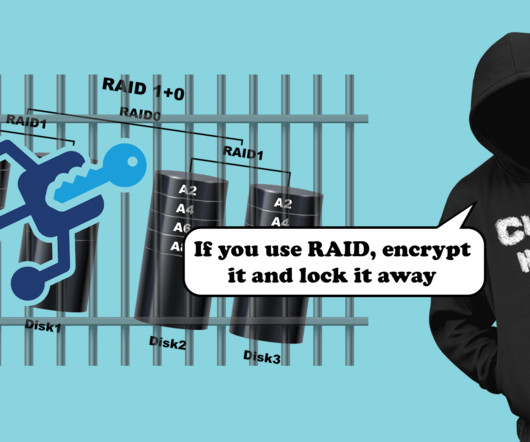
This led to a challenge – what was on the removed disc and did the data loss present a problem? The wider problem The data wasn’t encrypted. Disk encryption is critical here. If these disks lack encryption, sensitive data might be compromised. This allowed us to piece together the missing data.













































Let's personalize your content