Nation-state actors exploited two zero-days in ASA and FTD firewalls to breach government networks
Security Affairs
APRIL 24, 2024
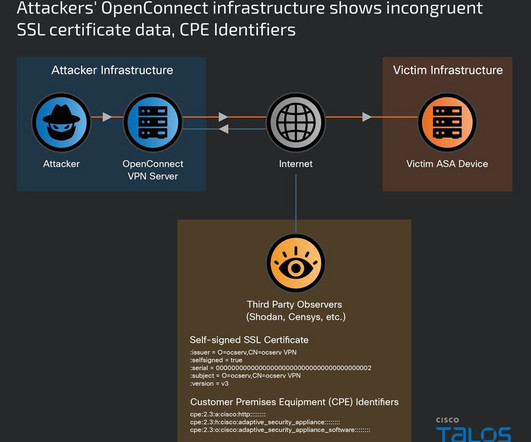
Nation-state actor UAT4356 has been exploiting two zero-days in ASA and FTD firewalls since November 2023 to breach government networks. By redirecting the pointer to the Line Dancer interpreter, attackers can interact with the device through POST requests without authentication.















































Let's personalize your content