Google Cybersecurity Action Team Threat Horizons Report #5 Is Out!
Anton on Security
JANUARY 3, 2023
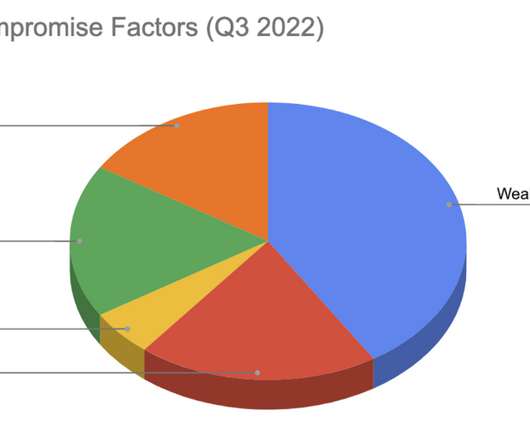
This also reminds me that if you are owned, your cloud environment is probably also owned…] “Mandiant research indicates that threat actors are increasingly targeting backups to inhibit reconstitution after an attack. not truly ‘new news’, but a useful reminder to those who assume, circa 2015, that ‘backups solve ransomware’.

















































Let's personalize your content