This World Backup Day, Our Customers Do the Talking
Webroot
MARCH 31, 2021
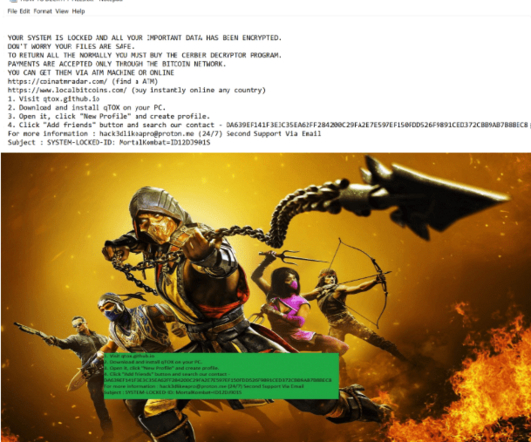
Are you taking the pledge this World Backup Day? Now in its tenth year, World Backup Day remains one of our favorite reminders of the risks of not backing up the data we hold dear. Numbers are great, and necessary for showing the scope of the problem, but I wanted to see how data loss—and backups—affect real people.

















































Let's personalize your content