GUEST ESSAY: Stolen logons, brute force hacking get used the most to breach web, email servers
The Last Watchdog
AUGUST 29, 2022
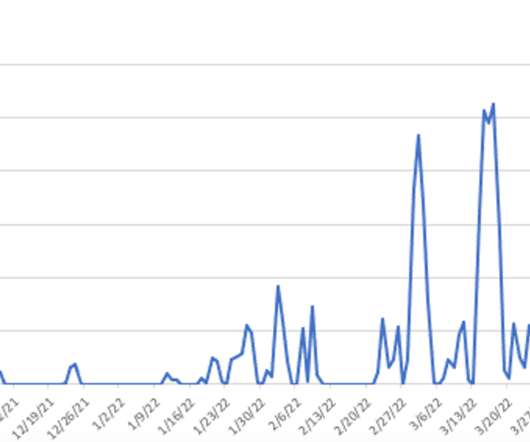
Web application attacks directed at organizations’ web and mail servers continue to take the lead in cybersecurity incidents. We’ve shared some helpful guidance on password security at Zigrin Security blog. From the chart, it is evident that many intrusions exploit the basic (mis)management of identity.








































Let's personalize your content