What Is CARTA? Continuous Adaptive Risk and Trust Assessment Explained
Heimadal Security
DECEMBER 15, 2022
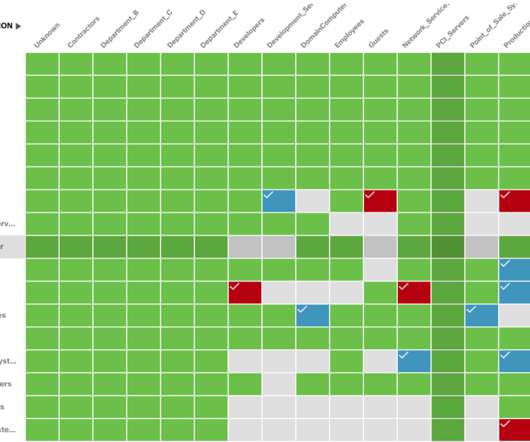
Continuous Adaptive Risk and Trust Assessment (CARTA) is an […]. Continuous Adaptive Risk and Trust Assessment Explained appeared first on Heimdal Security Blog. Digital services made for consumers are opening up new opportunities and vulnerabilities.


















































Let's personalize your content