Ransomware hackers adopting Intermittent Encryption
CyberSecurity Insiders
SEPTEMBER 13, 2022
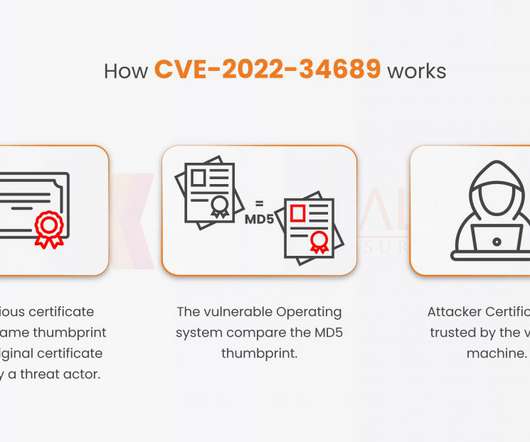
According to a study conducted by security firm SentinelOne, ransomware spreading hackers are adopting a new encryption standard named ‘Intermittent Encryption’ while targeting victims. Intermittent Encryption is nothing but locking down files on a partial note and at a great speed that also helps in being detected.











































Let's personalize your content