Hackers Are Going After Managed Security Providers
Heimadal Security
MAY 12, 2022
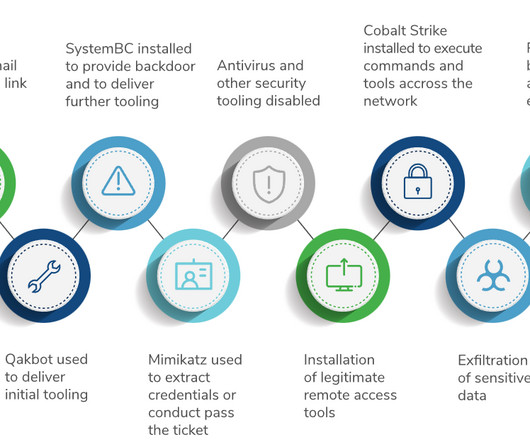
The post Hackers Are Going After Managed Security Providers appeared first on Heimdal Security Blog. ” These nations are signatories to the multilateral UKUSA Agreement, which is a pact for coordinating their efforts in the field of signals intelligence. .” What Happened?















































Let's personalize your content