GUEST ESSAY: Making the case for leveraging automation to eradicate cybersecurity burnout
The Last Watchdog
MAY 2, 2023
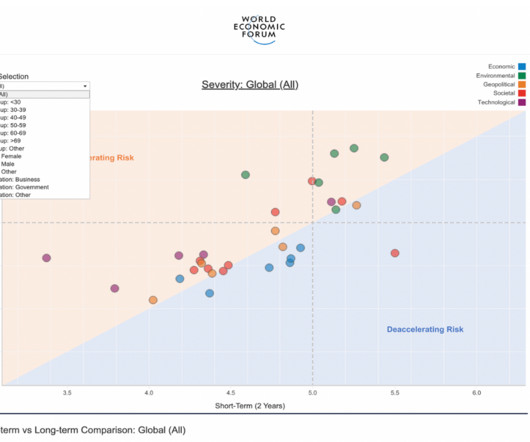
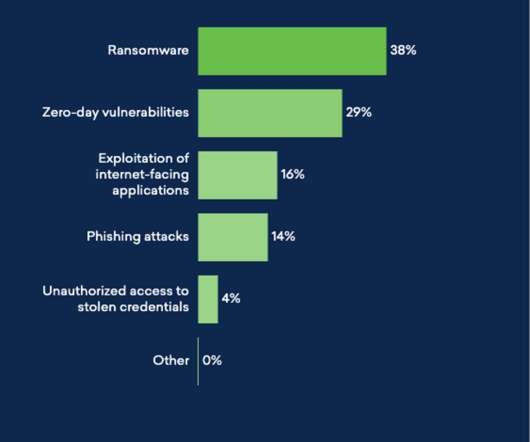
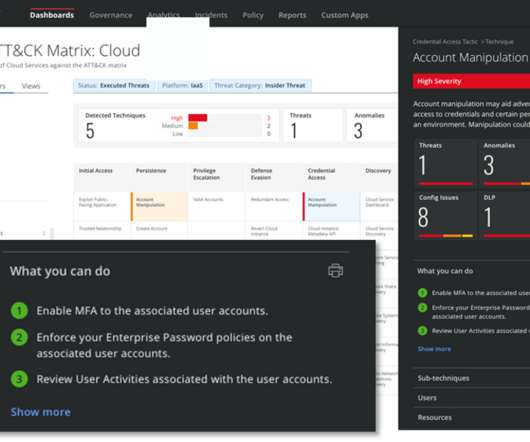
The rising complexity and prevalence of cybersecurity threats are making experts anxious. Related: Training employees to mitigate phishing It pressures working analysts to perform 24 hours’ worth of work in an 8-hour day. An increasingly digitized world means analysts can’t rest. Classify threat data.















































Let's personalize your content