How to Identify Phishing Emails and Prevent an Attack Using DNS Filtering
Heimadal Security
JULY 4, 2023
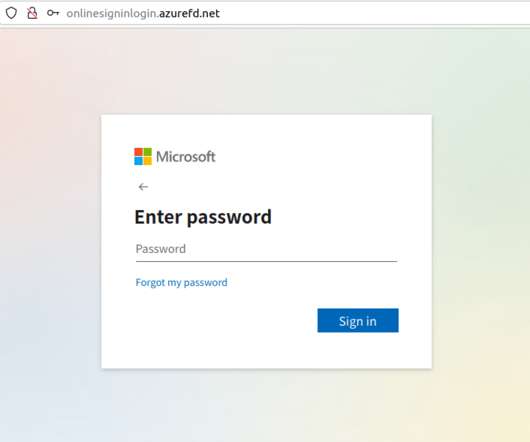
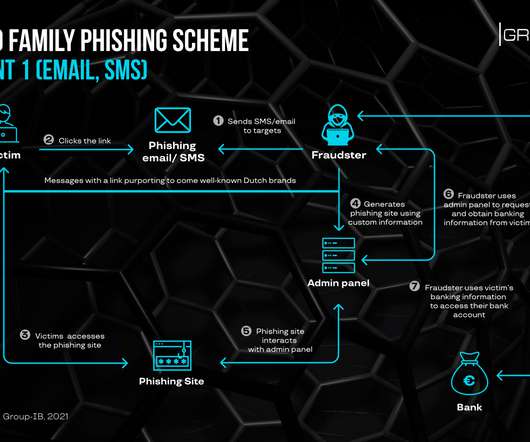
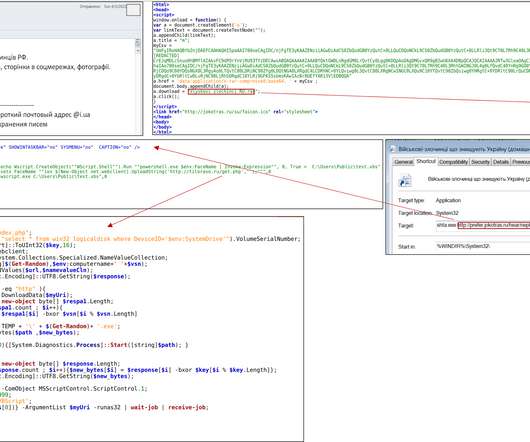
Identifying phishing emails and preventing phishing attacks continue to raise serious challenges for any company’s IT team. Although it`s been almost 30 years since the first phishing email was detected, threat actors still rely on this technique.















































Let's personalize your content