Open Source Threat Intelligence Platform – Best Alternatives for Your Company [2022]
Heimadal Security
JUNE 24, 2022
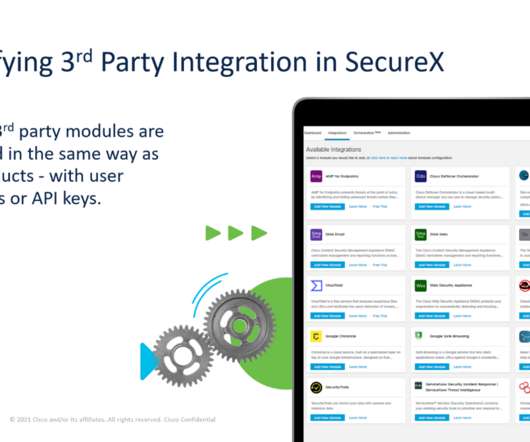
The technology that Threat Intelligence Platforms (TIP) employ allows companies to gather, aggregate, and manage threat intelligence data from a variety of sources and formats. Automation and simplification of the entire threat […].























Let's personalize your content