Does the World Need Cloud Detection and Response (CDR)?
Anton on Security
JUNE 23, 2022
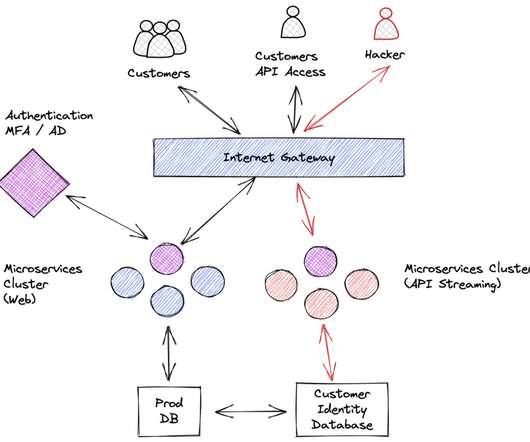
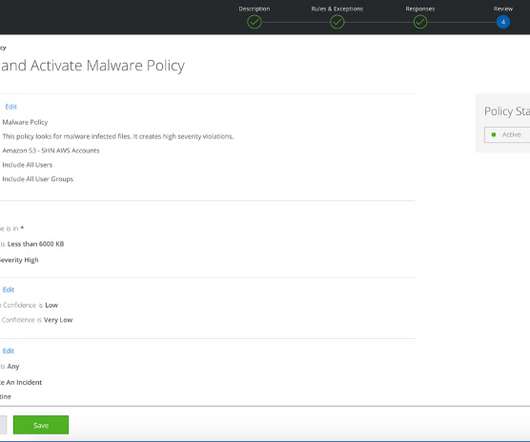
) So, let’s define CDR as a type of a security tool primarily focused on detecting, confirming and investigating suspicious activities and other security problems in various public cloud environments , including, but not limited to IaaS, PaaS, SaaS. To me, this provides additional motivation for CDR. I did NOT invent the term.






































Let's personalize your content