Threat Actors Use Search Engine Ads for Ransomware and Phishing Attacks
Heimadal Security
DECEMBER 22, 2022
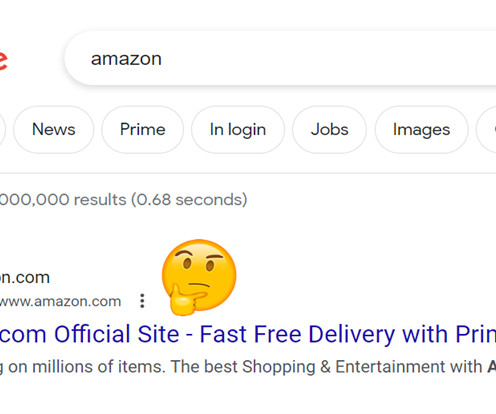
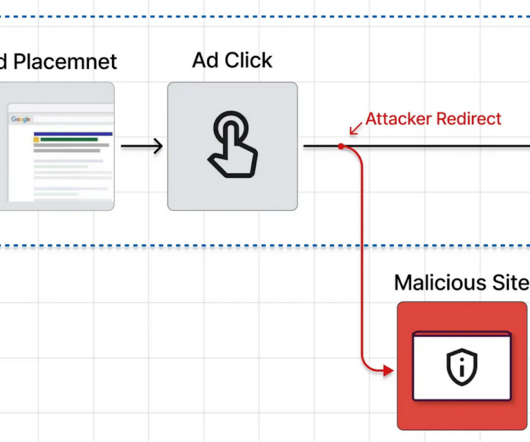
Threat actors use search engines to advertise websites that spread ransomware or steal login credentials. The ads for various impersonated businesses and services appear at the top of search results and guide the victim to websites that spoof almost perfectly the real ones.
















































Let's personalize your content