Sending Spammers to Password Purgatory with Microsoft Power Automate and Cloudflare Workers KV
Troy Hunt
AUGUST 3, 2022
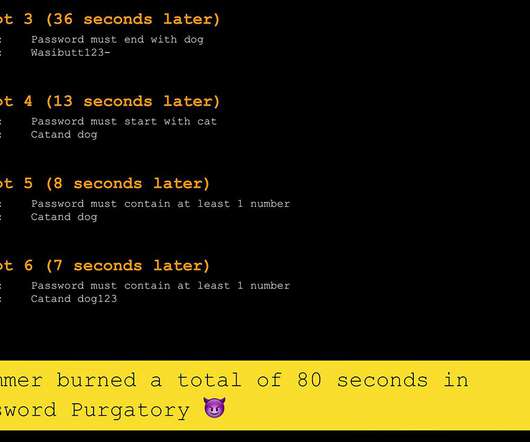
I opened-sourced it, took a bunch of PRs, built out the API to present increasingly inane password complexity criteria then left it at that. That page then embeds 2 scripts from the Password Purgatory website, both of which you can find in the open source and public Github repository I created in the original blog post.












































Let's personalize your content