How to Use Mayhem With Github Actions to Easily Secure Your Applications
ForAllSecure
MARCH 16, 2023
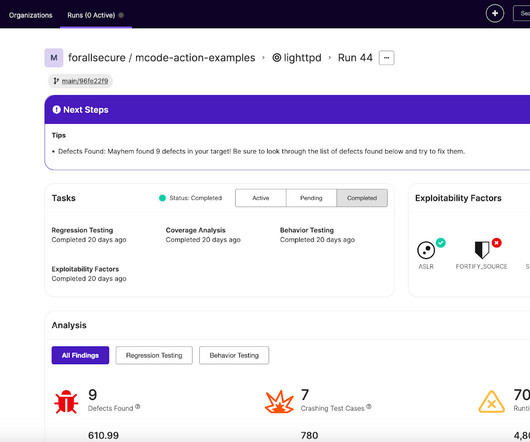
At ForAllSecure, our mission is to make security easy to use and easy to integrate with your existing development process. On that note, we’ve released our Mayhem GitHub Action , making it easier than ever to secure your applications using Mayhem in a GitHub CI/CD pipeline ( for free! ). The developer merges their fix.























Let's personalize your content