Microsoft Teams Phishing Attacks: Ransomware Group Shifts Tactics
Heimadal Security
SEPTEMBER 13, 2023
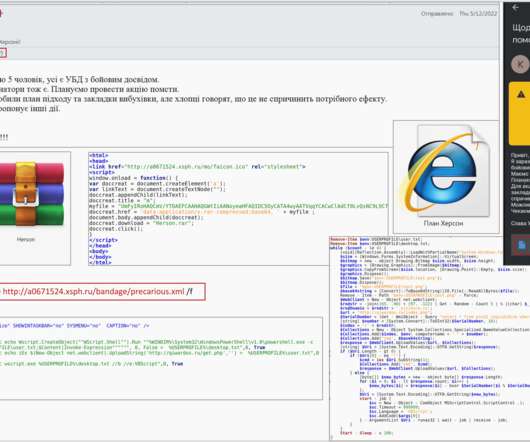
Storm-0324 recently moved from deploying ransomware to breaching corporate networks through Microsoft Teams phishing attacks. More about the Teams Phishing Attacks Microsoft stated […] The post Microsoft Teams Phishing Attacks: Ransomware Group Shifts Tactics appeared first on Heimdal Security Blog.











































Let's personalize your content