GUEST ESSAY: The Top 10 cybersecurity shortfalls that put SMBs, enterprises at elevated risk
The Last Watchdog
APRIL 17, 2023
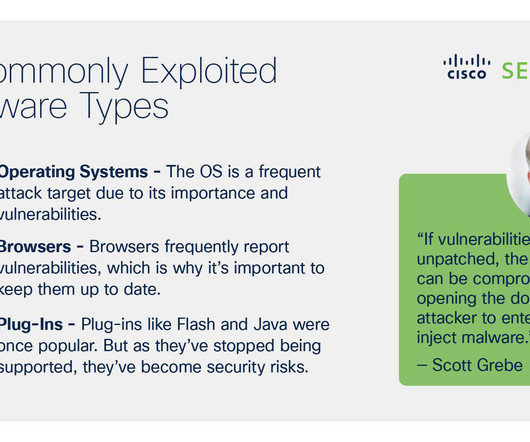
Related: Why timely training is a must-have That’s why businesses of all sizes need to understand the biggest cybersecurity weaknesses and take steps to mitigate them. Here are a few of the top security weaknesses that threaten organizations today: Poor risk management. Tick-in-the-box training.












































Let's personalize your content