What Is A Keylogger? Definition, Types, Examples and Prevention
Heimadal Security
OCTOBER 25, 2022
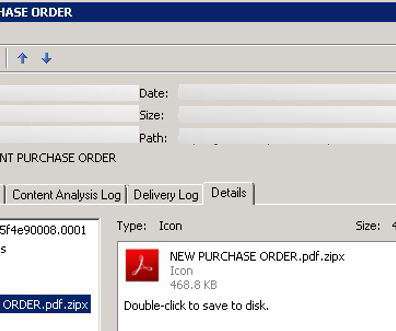
A keylogger is a software or hardware component that records everything typed on your computer’s keyboard. The term ‘keylogger’ comes from ‘keystroke logging’, the act of recording (logging) the keys that are pressed on a keyboard, usually without the user knowing that their actions are being watched. The post What Is A Keylogger?




























Let's personalize your content