Fla. Man Charged in SIM-Swapping Spree is Key Suspect in Hacker Groups Oktapus, Scattered Spider
Krebs on Security
JANUARY 30, 2024
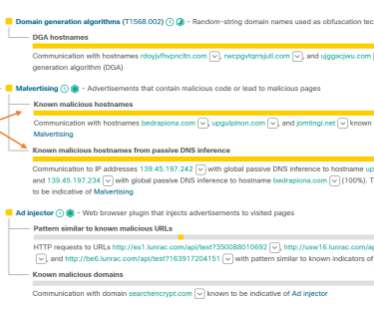
A graphic depicting how 0ktapus leveraged one victim to attack another. In each attack, the victims saw their email and financial accounts compromised after suffering an unauthorized SIM-swap, wherein attackers transferred each victim’s mobile phone number to a new device that they controlled. 9, 2024, U.S.
















































Let's personalize your content