OAuth Token: What It Is, How It Works, and Its Vulnerabilities
Security Boulevard
JULY 12, 2023
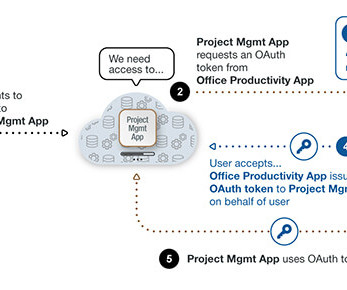
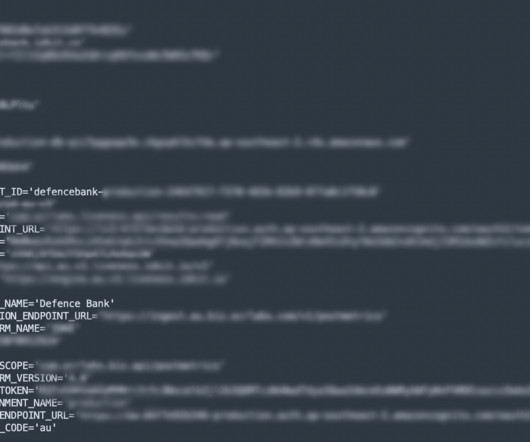
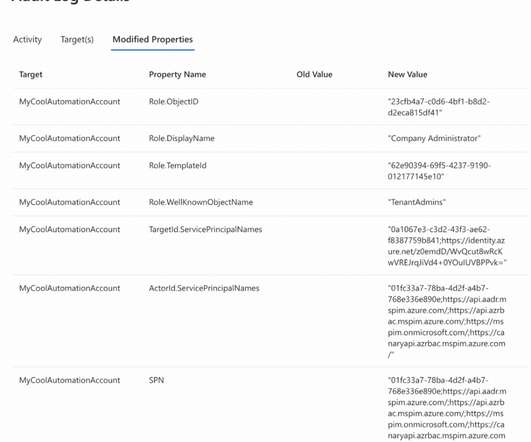
Learn how OAuth works and the risks of improper OAuth implementation that may introduce attack vectors on your SaaS estate. The post OAuth Token: What It Is, How It Works, and Its Vulnerabilities appeared first on AppOmni.





























Let's personalize your content