What Is Sensitive Information? How to Classify & Protect It
Digital Guardian
OCTOBER 30, 2023
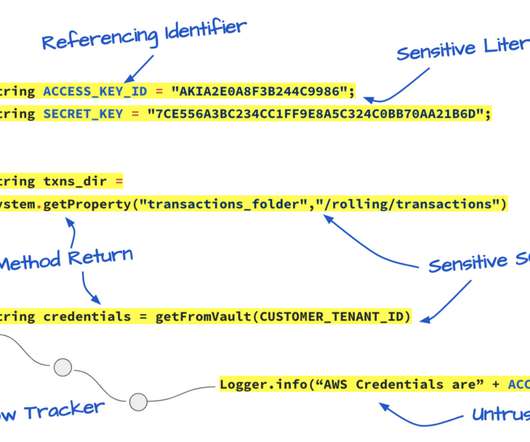
Curious how sensitive information differs from personal information? We break down examples, what can happen when that data is exposed, and best practices for protecting sensitive data in this blog.












































Let's personalize your content