The Battle for Attention: How Cybersecurity Fights for Truth in a World of Noise
Jane Frankland
JUNE 27, 2025
” This observation, from Chris Hayes’ book T he Sirens’ Call: How Attention Became the World’s Most Endangered Resource cuts to the heart of a growing challenge in every domain of modern society. Drop me a message on LinkedIn or book a call.










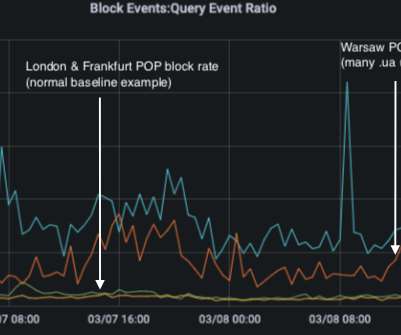














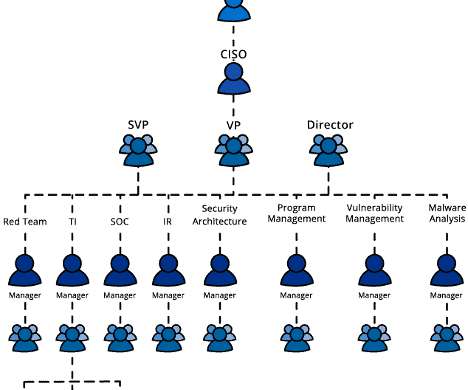

























Let's personalize your content