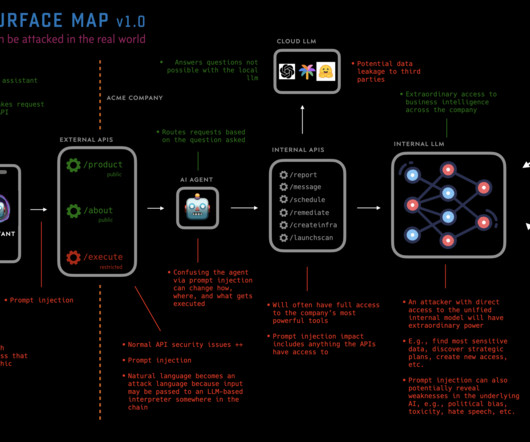
Analyzing IoT Security Best Practices
Schneier on Security
JUNE 25, 2020
van Oorschot: Abstract: Best practices for Internet of Things (IoT) security have recently attracted considerable attention worldwide from industry and governments, while academic research has highlighted the failure of many IoT product manufacturers to follow accepted practices. " by Christopher Bellman and Paul C.

















































Let's personalize your content