Pwn2Own 2021, more than $1,500,000 in cash and prizes for contestants
Security Affairs
JANUARY 27, 2021
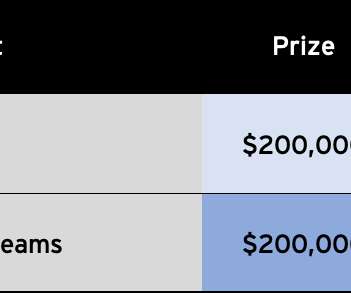
That’s one reason we added this new category and teamed up with Zoom to have them in the contest. A successful demonstration of an exploit in either of these products will earn the contestant $200,000 – quite the payout for a new category.” Microsoft Teams will also be a target. ” reads the announcement published by ZDI.










































Let's personalize your content