Cyber Threats Observatory Gets Improvements
Security Affairs
MAY 3, 2020
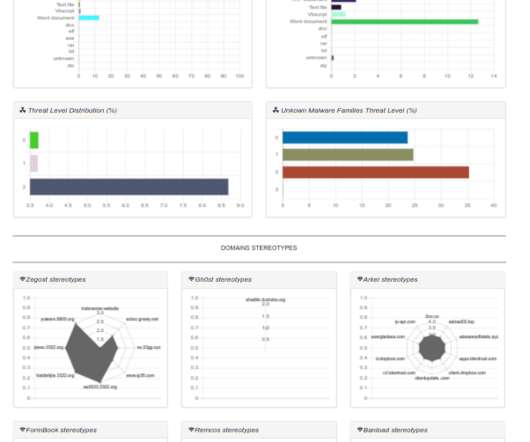
Today I am so happy to announce a big improvement in the cyber threats observatory (available for here ). Screenshot Cyber Threats Observatory ( HERE ). According to shared information, the Cyber Threats Observatory Dashboard is composed by the following sections: Malware Families Trends. What you find.














































Let's personalize your content