Social engineering: Cybercrime meets human hacking
Webroot
FEBRUARY 22, 2022
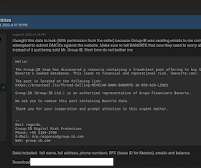
According to the latest ISACA State of Security 2021 report , social engineering is the leading cause of compromises experienced by organizations. Findings from the Verizon 2021 Data Breach Investigations Report also point to social engineering as the most common data breach attack method. Avoid becoming a victim.

















































Let's personalize your content