Now ransomware leads to three more additional Cyber Threats
CyberSecurity Insiders
APRIL 11, 2023
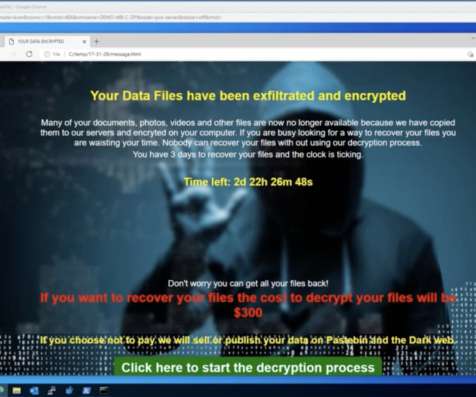
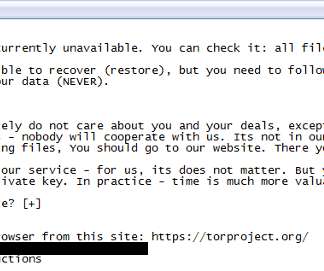
To almost all who are familiar with ransomware attacks, it just means data encryption until a ransom is paid. However, in recent years, especially after the first lockdown, hackers involved in spreading this file-encrypting tactic have evolved or changed their tactics to create more seriousness among victims. Yes, you read it right!














































Let's personalize your content