Choosing a Managed Security Service: MDR, Firewalls & SIEM
eSecurity Planet
OCTOBER 28, 2021
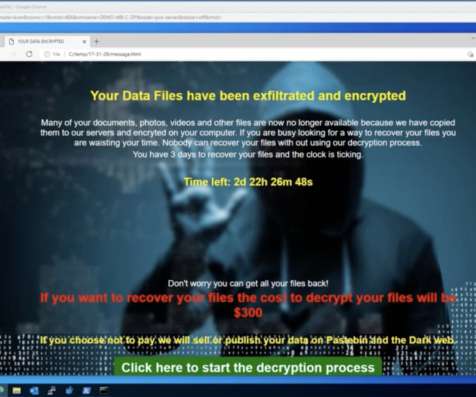
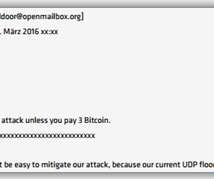
Many large enterprises struggle to stay on top of serious cyber threats like ransomware. We’ll take a look at managed SIEMs, managed firewalls, and MDR; how they differ; and where they can best help your organization. Managed Firewalls. For a small business, the challenge can seem overwhelming. Managed SIEM.

















































Let's personalize your content