Microsoft, Apple versus China, spyware actors
Tech Republic Security
SEPTEMBER 8, 2023
It’s a cat-and-mouse struggle as tech giants Microsoft and Apple deal with persistent threats from China state actors and Pegasus spyware.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
SEPTEMBER 8, 2023
It’s a cat-and-mouse struggle as tech giants Microsoft and Apple deal with persistent threats from China state actors and Pegasus spyware.

eSecurity Planet
SEPTEMBER 14, 2021
Apple continues to be haunted by spyware developed by an Israeli security firm that hostile governments used to hack into Apple devices to spy on journalists, activists and world leaders (see Apple Security Under Scrutiny Amid Fallout from NSO Spyware Scandal ). operating system was being exploited by the invasive Pegasus spyware.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Webroot
FEBRUARY 21, 2025
Cyber threats are no longer just the occasional virus or suspicious email. It combines multiple security capabilities into one easy-to-use package that includes: Antivirus protection Detects and neutralizes viruses, malware , spyware , and ransomware. Because in a world where cyber threats never rest, neither do we.

Security Affairs
FEBRUARY 10, 2022
I transcribed a recent interview, here some questions and answers about nation-state hacking, spyware, and cyber warfare. Enjoy” How has spyware changed the rules of cyber security in recent years? What will cyber security look like now that those tools are all over the internet? Pierluigi Paganini.

Security Affairs
NOVEMBER 17, 2024
Agency Warns Employees About Phone Use Amid Ongoing China Hack APT Actors Embed Malware within macOS Flutter Applications The Botnet is Back: SSC STRIKE Team Uncovers a Renewed Cyber Threat Iranian “Dream Job” Campaign 11.24

Security Affairs
APRIL 16, 2019
Scranos is a powerful cross-platform rootkit-enabled spyware discovered while investigating malware posing as legitimate software like video players, drivers and even anti-virus products. Despite the level of sophistication of the threat, the rootkit appears to be a work in progress, experts pointed out that it is continually evolving.”

Dark Reading
NOVEMBER 2, 2022
"SandStrike," the latest example of espionage-aimed Android malware, relies on elaborate social media efforts and back-end infrastructure.

Penetration Testing
JUNE 15, 2025
Insikt Group reveals Predator spyware's resurgence, with new infrastructure, obfuscation, and a previously unreported customer in Mozambique, despite sanctions.

Security Affairs
JULY 5, 2025
Agencies warn of ongoing Iranian cyber threats to critical infrastructure U.S. Iran retaliates with missile barrages How Geopolitical Tensions Are Shaping Cyber Warfare Cybersecurity Facebook is asking to use Meta AI on photos in your camera roll you haven’t yet shared Ahold Delhaize Data Breach Impacts 2.2

Krebs on Security
SEPTEMBER 14, 2022
Kevin Breen , director of cyber threat research at Immersive Labs , said any vulnerability that is actively targeted by attackers in the wild must be put to the top of any patching list. privilege escalation vulnerabilities are often highly sought after by cyber attackers,” Breen said.

CyberSecurity Insiders
JANUARY 5, 2022
Highly placed sources say that the malware has been distributed via phishing campaign by a cyber threat group named MalSmoke. Keeping the systems loaded with anti-spyware or antivirus software makes complete sense.
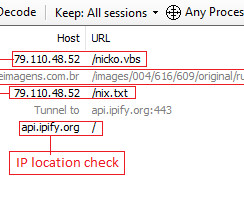
Security Affairs
DECEMBER 21, 2023
Threat actors are exploiting an old Microsoft Office vulnerability, tracked as CVE-2017-11882 (CVSS score: 7.8), as part of phishing campaigns to spread the Agent Tesla malware. Agent Tesla is a spyware that is used to spy on the victims by collecting keystrokes, system clipboard, screenshots, and credentials from the infected system.

CyberSecurity Insiders
JULY 20, 2021
Google Cloud IDS was also unveiled by the web search giant that solely depends on the Palo Alto Networks threat detection technology that helps detect malware, spyware, command-and-control software attacks, and other network based threats hitting the cloud platform.

SecureWorld News
OCTOBER 5, 2023
Callie Guenther, Senior Manager of Cyber Threat Research at Critical Start, shared her thoughts with SecureWorld News: "Apple's growing popularity and expanding market share make them prime targets for advanced adversaries. So, what is really driving this rapid increase in 2023?

Security Affairs
MARCH 8, 2025
Quantum computers threaten to break online security in minutes, expert warns ENISA NIS360 2024 Catalan court says NSO Group executives can be charged in spyware investigation Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs hacking,newsletter)

Security Affairs
AUGUST 21, 2024
The Vermin group attempted to deploy two malicious codes in this campaign, the previously known Spectr spyware, and a new malware family dubbed Firmachagent. In June 2024, Ukraine CERT-UA warned of cyber attacks targeting defense forces with SPECTR malware as part of another cyber espionage campaign dubbed SickSync.

SecureWorld News
NOVEMBER 21, 2023
The report, titled " Predator Files: Caught in the Net ," delves into the operations of the "Intellexa alliance," a complex network of interconnected companies that develop and market powerful spyware used to monitor and manipulate individuals worldwide. Cytrox is now part of Intellexa."

IT Security Guru
APRIL 26, 2021
Spyware – Without realising it, gamers could be targeted through spyware schemes, especially if they are dealing with an untrustworthy online gaming operation. Spyware monitors a user’s every movement and actions on the internet without their knowledge. Tackling these cyber threats as an online gamer.

CyberSecurity Insiders
DECEMBER 27, 2021
So, all those accessing such websites on office devices, better be aware of this cyber threat before it is too late. Note- From the past few days, some media houses are running rampant reports that the pirated movie copies of “Spider Man No Way Home” might be riddled with crypto mining and blister malware.

CyberSecurity Insiders
NOVEMBER 1, 2021
Use passcodes and anti-spyware programs. Since phishing attempts infect an individual’s system with malware, spyware, or viruses, it’s critical to use dedicated programs installed on all gadgets and throughout your system. Once you cover the hardware and cloud, focus on the network.

SecureWorld News
JULY 10, 2023
The Google Play Store, a widely-trusted source for Android applications, has recently become a battleground for a concerning wave of spyware with ties to China. Pradeo, the mobile security company that discovered these malicious apps, has released a report discussing the spyware lurking on the Google Play Store. million users.

Malwarebytes
MAY 20, 2024
The constant barrage of cyber threats can be overwhelming for all of us. And, as those threats evolve and attackers find new ways to compromise us, we need a way to keep on top of everything nasty that’s thrown our way. Rapid response When Malwarebytes detects suspicious activity or potential threats, it responds quickly.

Security Affairs
JUNE 29, 2025
House banned WhatsApp on government devices due to security concerns Russia-linked APT28 use Signal chats to target Ukraine official with malware China-linked APT Salt Typhoon targets Canadian Telecom companies U.S.

Hacker's King
MAY 24, 2025
In the contemporary and advanced society, cyber threats are on the rise in both quantity and sophistication. While these octopi of terror could spring from many sources, do you know what the very wellspring of most cyber attacks is? Different types of malware include viruses, worms, spyware, ransomware, and trojans.

Trend Micro
SEPTEMBER 16, 2021
2021 Midyear Cybersecurity Report and Apple emergency patches fix zero-click iMessage bug used to inject NSO spyware.

CyberSecurity Insiders
OCTOBER 12, 2021
Cameron added that most of the cyber threat actors were interested in stealing COVID related research information from the past 8 months and now they have indulged in COVID themed attacks for scamming the populace.

The Last Watchdog
JANUARY 28, 2019
There is a distinct burden for each person using Internet services to help dampen cyber threats that are as diverse as they are dynamic. Apps from other sources can carry malware or spyware. Through the course of this year, Gartner forecasts that the infosec market will climb 9 percent to $124 billion.
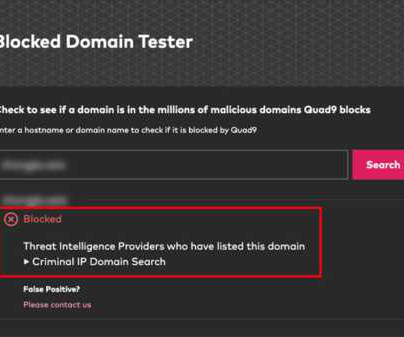
The Last Watchdog
MAY 13, 2024
May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users.

Digital Shadows
NOVEMBER 10, 2022
Cyber threat actors, with varying resources and motivations, are highly interested in these eye-catching events too. For instance, financially-motivated threat actors often plant in malicious URLs spoofing these events to fraudulent sites, hoping to maximize their chances of scamming naive internet users for a quick (illicit) profit.

The Last Watchdog
MAY 2, 2019
That said, it’s also clear that all too many SMBs remain ill equipped to assess evolving cyber threats, much less effectively mitigate them. According to the Cyberthreat Index, 45 percent of all SMBs and 56% of large SMBs believe they are vulnerable to “imminent” threats of cybersecurity attacks.

Security Affairs
MARCH 24, 2024
Government’s Antitrust Case Against Apple Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, Ramadan )

SecureWorld News
SEPTEMBER 28, 2020
Even though Google is very much aware of this cyber threat, it manages to keep finding its way into their official application market. Google has removed 17 apps from its Google Play store due to malware known as Joker. The Joker malware family is infamous for constantly targeting Android devices.

Security Affairs
APRIL 20, 2025
infrastructure International Press Newsletter Cybercrime Pixel-Perfect Trap: The Surge of SVG-Borne Phishing Attacks Threat actors misuse Node.js

eSecurity Planet
JUNE 16, 2022
The 2022 SonicWall Cyber Threat Report found that all types of cyberattacks increased in 2021. Encrypted threats spiked 167%, ransomware increased 105%, and 5.4 Also read: Mobile Malware: Threats and Solutions. Phishing attacks continue to dominate cyber threats. Crimeware and spyware.

Security Affairs
APRIL 21, 2024
PoC publicly available Linux variant of Cerber ransomware targets Atlassian servers Ivanti fixed two critical flaws in its Avalanche MDM Researchers released exploit code for actively exploited Palo Alto PAN-OS bug Cisco warns of large-scale brute-force attacks against VPN and SSH services PuTTY SSH Client flaw allows of private keys recovery A renewed (..)

SiteLock
AUGUST 27, 2021
But you may wonder what exactly malware is, and why it’s such a serious threat to your website and your site’s visitors. Spyware is malware that is installed on a user’s device without their permission and steals their data. What is Malware?

Hot for Security
JUNE 14, 2021
While some security experts might seem over-zealous shouting about the dangers, the vast majority of warnings about mobile security threats are indeed justified. Just because our phones are not tethered physically to a network doesn’t mean they’re safe from cyber threats. Platform-agnostic threats. Weaponizing hype.

Hot for Security
JUNE 15, 2021
Given the portability and myriad of functionalities, mobile devices are highly susceptible to cyber threats, including malware, spyware and phishing attempts that may compromise that precious piece of tech we keep in our pocket and any information stored on it.

Security Affairs
JULY 14, 2024
Their focus? million miles on U.S. roads, collecting detailed data with cameras and lasers Shopify denies it was hacked, links stolen data to third-party app The July 2024 Security Update Review Can AI be Meaningfully Regulated, or is Regulation a Deceitful Fudge?

Webroot
OCTOBER 4, 2024
Spyware : Secretly monitors your online behavior and shares your personal information. Last year alone, there were more than 6 billion malware attacks detected worldwide. Some of the many forms of malware include: Ransomware : Prevents you from accessing your files, devices or network unless you pay money.

CyberSecurity Insiders
MAY 19, 2021
People are increasingly becoming aware of the threats posed by hackers who infiltrate devices using viruses, spyware and malware. However, it may be time to shine the spotlight on “stalkerware”, a completely different type of cyber security threat that nevertheless has lasting negative repercussions.

eSecurity Planet
JUNE 7, 2022
NINJIO prepares organizations to defend against cyber threats through their engaging, video-based training courses. It needs to be maintained for various types of cyber threats like Ransomware, Malware, Social Engineering, and Phishing. Top Cybersecurity Companies. NINJIO Cybersecurity Awareness Training. Visit website.

Malwarebytes
JANUARY 25, 2024
The NCSC confirmed, saying: “All types of cyber threat actor – state and non-state, skilled and less skilled – are already using AI, to varying degrees.” Professional spyware vendors have deep enough pockets to invest in new tools, training, and development. But that availability will undoubtedly grow.

eSecurity Planet
SEPTEMBER 29, 2021
Recent research by Positive Technologies looked at the cyber threat landscape during Q2 2021 and found that ransomware attacks reached “stratospheric” levels, accounting for 69% of all malware attacks, a huge jump from 39% in Q2 2020. Rapid malware scan for quick and easy detection of threats. Scan scheduling.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content