Spyware, ransomware and Nation-state hacking: Q&A from a recent interview
Security Affairs
FEBRUARY 10, 2022
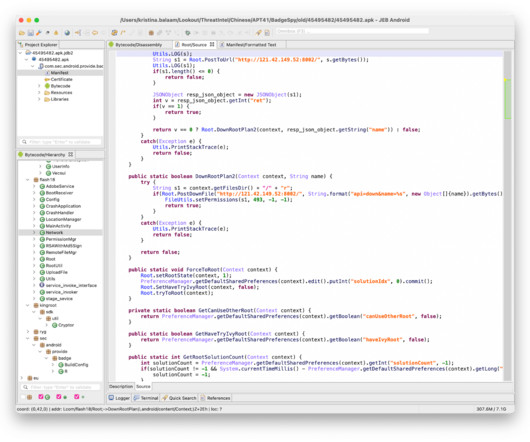
I transcribed a recent interview, here some questions and answers about nation-state hacking, spyware, and cyber warfare. Enjoy” How has spyware changed the rules of cyber security in recent years? Spyware are powerful weapons in the arsenal of governments and cybercrime gangs.
















































Let's personalize your content