Lumu Raises $7.5M to Advance Threat Detection
Security Boulevard
MARCH 10, 2021
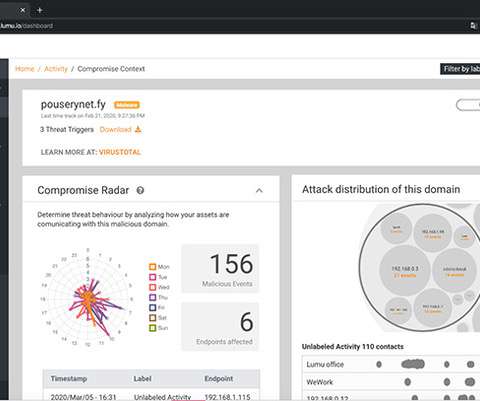
Ricardo Villadiego, Lumu CEO, said Lumu collects and standardizes metadata from across the network, including DNS queries, network flows, access logs from perimeter proxies. to Advance Threat Detection appeared first on Security Boulevard. Lumu announced today it has raised an additional $7.5 The post Lumu Raises $7.5M
















































Let's personalize your content