RSAC insights: SolarWinds hack illustrates why software builds need scrutiny — at deployment
The Last Watchdog
MAY 11, 2021
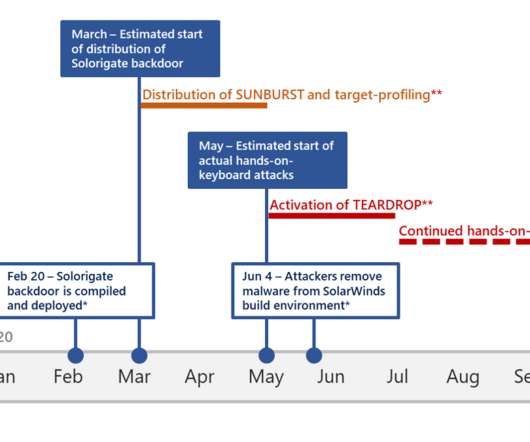
The payload malware: Sunburst, a heavily-obfuscated backdoor. People tend to focus on the Sunburst malware , the actual backdoor that ended up in the affected update package,” Pericin told me. Out of this comes whitelists and blacklists on which malware filters are based. Granular scrutiny.




































Let's personalize your content