Moobot botnet is back and targets vulnerable D-Link routers
Security Affairs
SEPTEMBER 7, 2022
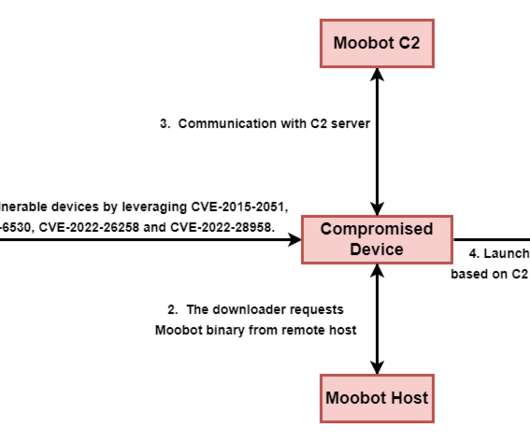
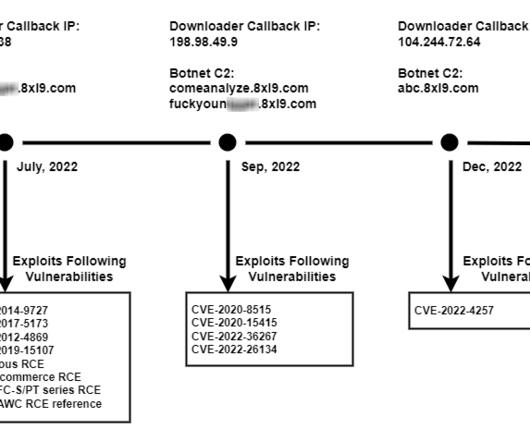
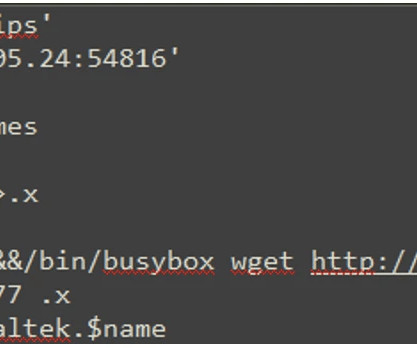
Threat actors explored the four D-Link vulnerabilities to gain remote code execution and download a MooBot downloader from 159.203.15[.]179. Once the attacker gains control in this manner, they could take advantage by including the newly compromised devices into their botnet to conduct further attacks such as DDoS.”










































Let's personalize your content