MIT Report Spotlights Triple Threat Fueling Data Breach Tsunami
SecureWorld News
JUNE 4, 2024
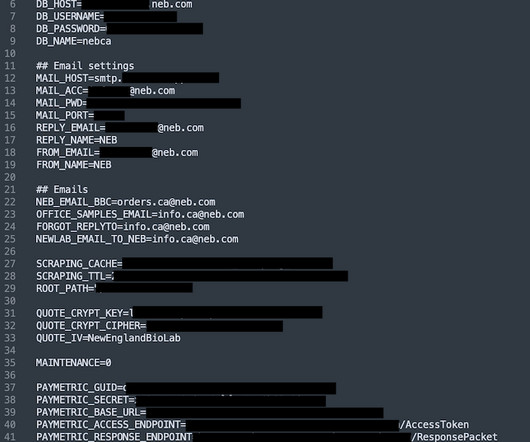
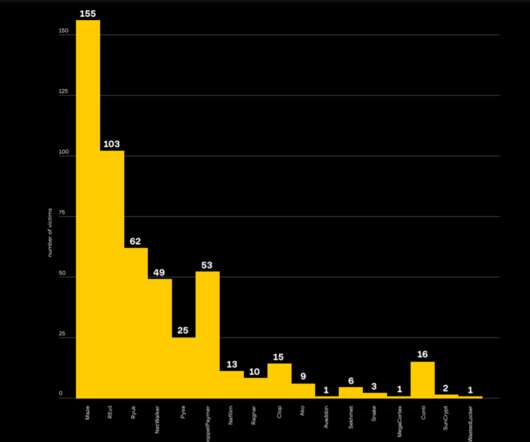
As high-profile data breaches and leaks continue making headlines, a new report from Massachusetts Institute of Technology (MIT) examines the triple-whammy of factors enabling this tidal wave of personal data theft. Infostealer attacks are on the rise, focusing on data collection rather than just hiding data behind encryption.











































Let's personalize your content