A compelling story
Cisco Security
JUNE 13, 2022
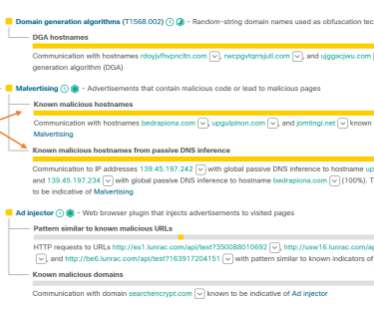
For example, the security event might involve requests to communicate with an IP address, and the analyst would say, “This IP address belongs to my DNS server, so the traffic is legitimate.” Wait, what is the baseline, and how was it violated in this particular security event?” Annotated security events.

























Let's personalize your content