Lumu Raises $7.5M to Advance Threat Detection
Security Boulevard
MARCH 10, 2021
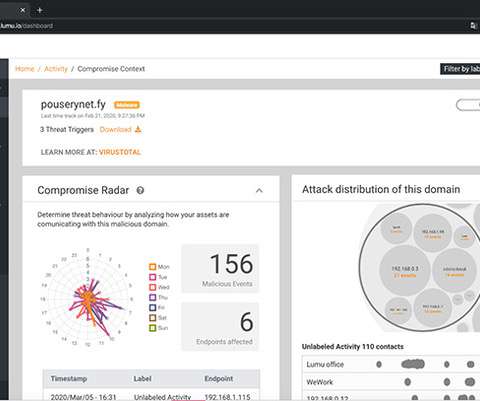
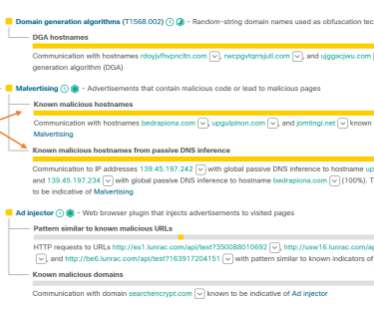
million to fuel adoption of a cloud-based platform that employs machine learning algorithms to surface the highest priority security alerts in real-time. Ricardo Villadiego, Lumu CEO, said Lumu collects and standardizes metadata from across the network, including DNS queries, network flows, access logs from perimeter proxies.
































Let's personalize your content