Microsoft releases open-source tool for checking MikroTik Routers compromise
Security Affairs
MARCH 17, 2022
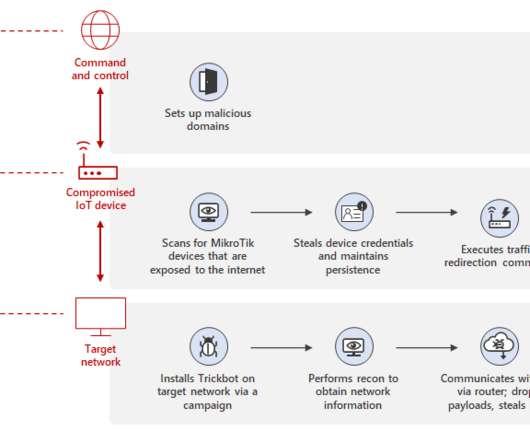
Recently Check Point researchers reported that the infamous TrickBot malware was employed in attacks against customers of 60 financial and technology companies with new anti-analysis features. The news wave of attacks aimed at cryptocurrency firms, most of them located in the U.S. Follow me on Twitter: @securityaffairs and Facebook.





























Let's personalize your content