Better Supporting the Have I Been Pwned API with Zendesk
Troy Hunt
NOVEMBER 3, 2022
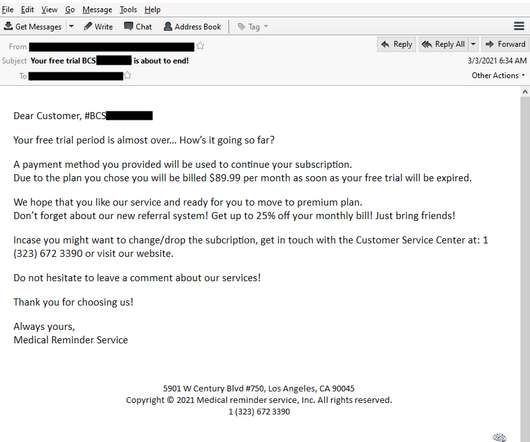
The API is actually pretty simple: plug in an email address, get a result, and that's a very clearly documented process. But where things get more nuanced is when people pay money for it because suddenly, there are different expectations. For example, how do you cancel a subscription once it's started?








































Let's personalize your content