Ukraine claims it hacked Russian Ministry of Defence, stole secrets and encryption ciphers
Graham Cluley
MARCH 6, 2024
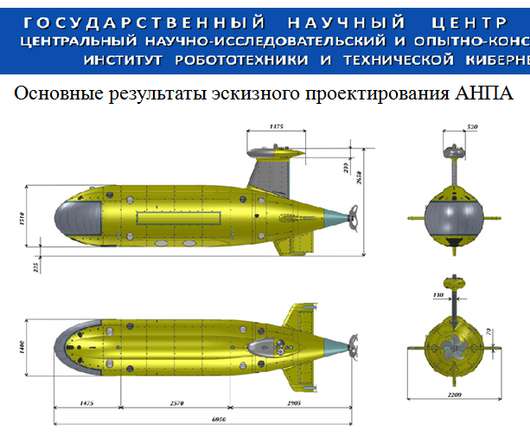
Ukraine claims its hackers have gained possession of "the information security and encryption software" used by Russia's Ministry of Defence , as well as secret documents, reports, and instructions exchanged between over 2,000 units of Russia's security services.

































Let's personalize your content