Phishing uses Colonial Pipeline ransomware lures to infect victims
Bleeping Computer
JUNE 4, 2021
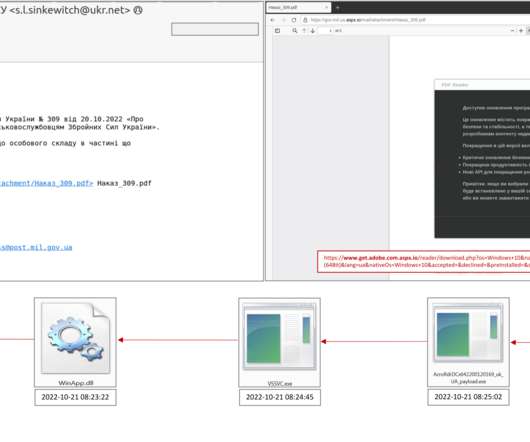
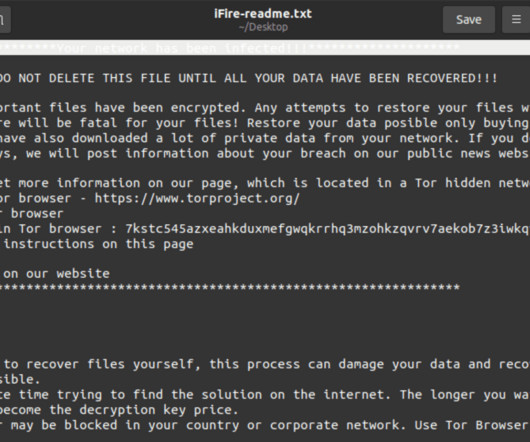
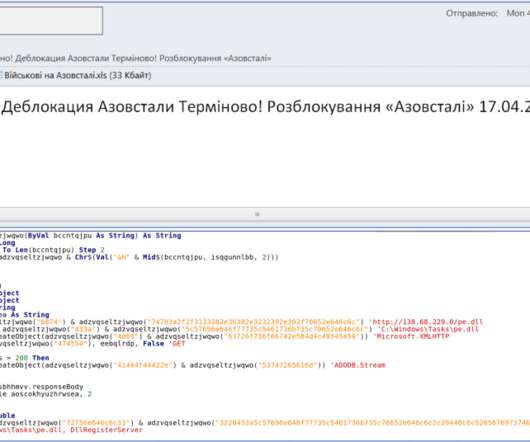
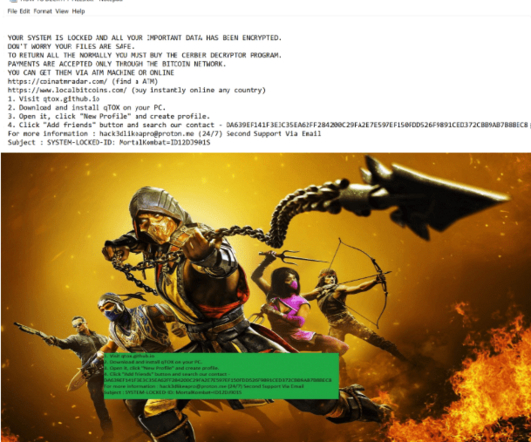
The recent ransomware attack on Colonial Pipeline inspired a threat actor to create create a new phishing lure to trick victims into downloading malicious files. [.].












































Let's personalize your content