News alert: Seraphic launches BrowserTotal™ — a free AI-powered tool to stress test browser security
The Last Watchdog
JUNE 9, 2025
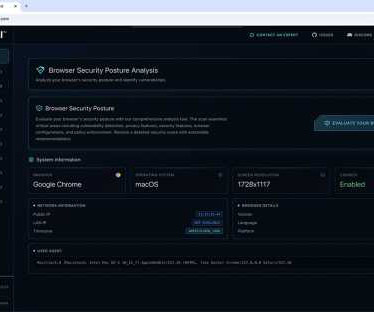
The launch coincides with the Gartner Security & Risk Management Summit 2025, where Seraphic will be showcasing the new platform with live demos at booth #1257. Powered by AI, Browser Total offers CISOs and security teams a comprehensive, hands-on environment to test browser security defenses against today’s most sophisticated threats.















































Let's personalize your content