Phishers Spoof USPS, 12 Other Natl’ Postal Services
Krebs on Security
OCTOBER 9, 2023
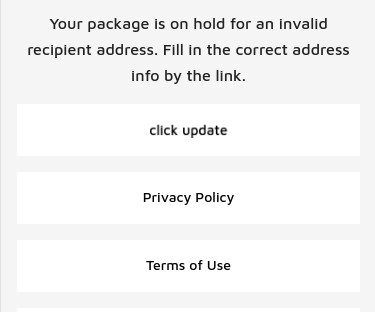
The fake USPS phishing page. Recent weeks have seen a sizable uptick in the number of phishing scams targeting U.S. Postal Service (USPS) customers. Here’s a look at an extensive SMS phishing operation that tries to steal personal and financial data by spoofing the USPS, as well as postal services in at least a dozen other countries. KrebsOnSecurity recently heard from a reader who received an SMS purporting to have been sent by the USPS, saying there was a problem with a package destined






































Let's personalize your content